Implementing a secure terraform IaC pipeline with Github actions for EKS

About the Customer
Our customer is a clinical research organization primarily focusing on clinical trials and bringing new treatments to patients faster and safer.
THE PRE- STATE
As a healthcare tech services provider, our customer faced the challenge of provisioning environments repeatedly for product development and testing. There was no control or overall visibility over the infrastructure code deployed by the developers. The need for a comprehensive security framework and expertise was high. Without it, the team faced a delay in the identification and remediation of high-risk issues, leading to delayed service launches.
THE POST STATE
Our solution reduced incidents from misconfigurations or compatibility issues, improving infrastructure stability by 40% and eliminating unnecessary infrastructure components with a 10% savings. The well-defined pipeline enabled the team to deploy faster and release new features quicker, resulting in a 25% lesser provisioning time. Incorporating security into the pipeline brought down security
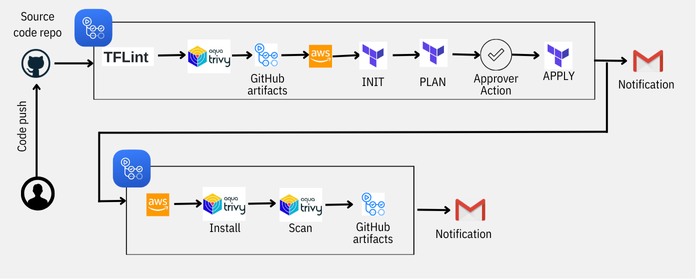
BRIDGE
Our team set up a dedicated GitHub code repository that allowed changes to the Terraform code to be monitored. GitHub Actions was the recommended CI/CD platform configured for the pipeline. Security scans were integrated with the pipeline ensuring that the infrastructure and code were scanned for vulnerabilities or misconfigurations. TFlint and Aquasec Trivy were the chosen scanning tools for security issues. The teams received notifications and alerts are configured to address any security vulnerabilities promptly.